News
Ping Identity Solution Preview for Azure AD Coming Soon
This week will bring the preview of Ping Identity, which aims to streamline single sign-on access to header-based Web applications, in Azure Active Directory.
On Friday, March 24, Microsoft plans to roll out an Azure Active Directory Premium preview technology that will facilitate single sign-on access to so-called "legacy" Web applications, according to an announcement. These Web applications might be located on premises, or they might be cloud-based services, but they depend on the use of headers as part of the user-access validation process. The preview will include PingAccess technology that's been integrated into the Azure Active Directory Premium service to enable the Azure AD Application Proxy service to work with these kinds of Web apps.
"Our customers have consistently asked for [Azure AD] Application Proxy to also support apps that use headers for authentication, such as PeopleSoft, NetWeaver Portal, and WebCenter," explained Harshini Jayaram, a program manager on the Azure Active Directory team, in Microsoft's announcement. "To enable this capability for our Azure AD Premium customers, we have partnered with Ping Identity. Ping Identity's PingAccess now allows Application Proxy to support apps that use header-based authentication."
Azure AD supports single sign-on authentications for Web apps that use open protocols, such as SAML, OAuth 2.0 and Kerberos. That authentication process continues. However, for those Web apps that require headers for authentication, the PingAccess technology in Azure AD Premium will take charge, if the PingAccess for Azure AD solution gets installed in an organization's premises-based infrastructure.
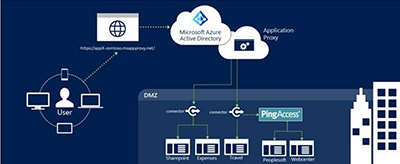
No virtual private network or demilitarized zone (DMZ) is required when using integrated PingAccess technology. Here's how the process works, according to a Ping Identity blog post:
- When requesting access, the Microsoft App Proxy redirects to PingAccess.
- PingAccess sends users to Azure AD for authentication as necessary.
- PingAccess converts Azure AD authentication tokens to HTTP header attributes.
- The web application uses the header attributes to grant user access.
Microsoft's announcement explained that only outbound connections are part of this authentication process. The process is illustrated in the following diagram:
 [Click on image for larger view.]
PingAccess used with Azure Active Directory Premium for authenticating header-based Web apps. Source: Microsoft blog.
[Click on image for larger view.]
PingAccess used with Azure Active Directory Premium for authenticating header-based Web apps. Source: Microsoft blog.
Azure Active Directory Premium subscribers have some free authentications using the PingAccess technology, but it's just for 20 applications maximum. For more apps, organizations would need to purchase PingAccess licensing from Ping Identity.
While this feature will reach the preview stage on Friday, the "general availability" or production-environment release of PingAccess in Azure AD Premium is "expected before the end of June 2017," according to Ping Identity's blog post.
Ping Identity also offers a PingFederate product with greater support for "identity federation, modern web and API access security and multi-factor authentication," according to its Web page description.
In September, when Microsoft had announced the partnership effort, it indicated that the two companies also were working together to add PingFederate technology to Azure AD Connect. Organizations typically use Azure AD Connect, a wizard-like tool, to set up connections with Microsoft's cloud-based identity and access management service.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.