News
Microsoft Demos Windows 10 Credential Guard
Microsoft this week started showing off Windows 10's security virtualization feature called Credential Guard.
The demo by Ben Armstrong, a Hyper-V program manager at Microsoft, showed how a machine enabled with Credential Guard can block access attempts by attackers or malware. He explained that previous Windows versions used the Local Security Authority (also known as "LSASS.EXE") to store credential information. With Windows 10 and Device Guard, credentials are stored encrypted using Hyper-V, an approach known as "virtualization-assisted security." Credential Guard blocks access "even when an untrusted program has full administrative access to your environment," Armstrong explained.
Here's Microsoft's one-sentence definition of Credential Guard, according to a spokesperson:
Credential Guard is the ability to store derived credentials (i.e. NTLM hashes and Kerberos tickets) and the process that manages them (i.e. Local Security Authority Subsystem Service (LSASS)), in a secured isolated container which uses Hyper-V and virtualization based security (VBS) for additional protections.
The Credential Guard feature is just available with the Windows 10 Enterprise or Education editions. It's not available with Windows 10 Pro. In addition, Credential Guard has specific hardware requirements, namely:
- Unified Extensible Firmware Interface (UEFI) 2.3.1 or greater;
- Virtualization Extensions such as Intel VT-X, AMD-V and SLAT must be enabled;
- x64 version of Windows;
- IOMMU, such as Intel VT-d, AMD-Vi;
- TPM 2.0;
- BIOS lockdown
The idea of Credential Guard is to prevent credential theft, which can lead to pass-the-hash types of attacks. Microsoft's Lex Thomas explained in a Microsoft Channel 9 video that most people think of security breaches as happening because some algorithm was hacked. However, about 80 percent to 90 percent of those breaches result from credential theft.
Microsoft's virtualization-assisted security in Windows 10 is based on an Isolated User Mode (IUM) technology. Once an attacker has administrative privileges or "debug credentials" on a machine, then it's possible to pull from the memory space of the operating system. However, with IUM, there's a boundary and the credentials are encrypted. Drivers can't get into the Local Security Authority of Windows 10 and strict signing is enforced in the IUM, explained Brantley Whitley, in the Channel 9 video. Whitley presented this slide illustrating the concept:
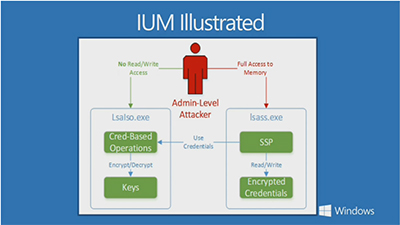 [Click on image for larger view.]
Isolated User Mode (IUM) works to block access to the Local Security Authority in Windows 10. Source: Microsoft Channel 9 video.
[Click on image for larger view.]
Isolated User Mode (IUM) works to block access to the Local Security Authority in Windows 10. Source: Microsoft Channel 9 video.
He explained that previous Windows versions had permitted drivers to inject code into the LSA. Credentials could be compromised and then used to access other machines.
Credential Guard gets managed by IT pros using specific Group Policy Objects. The feature has to be turned on, and its hardware and software requirements need to be met, for Credential Guard to work. Whitley added that the weaker MS-CHAPv2 and NTLMv1 encryption protocols need to be disabled. Credential Guard will work with "down-level domain controllers and network resources," he added.
Microsoft this month updated its TechNet article describing Credential Guard. The technology has some limits. It doesn't protect credentials stored in Credential Manager or in software that saves passwords, including local accounts and Microsoft accounts. It also can't protect against key loggers.
Windows 10 also has another virtualization-assisted security feature called "Device Guard," which has similar requirements to Credential Guard. Device Guard prevents non-trusted applications from running on a Windows 10 machines. It allows organizations to control what's run on a machine by locking it down. Device Guard is controllable via Group Policy, mobile device management and PowerShell, according to a Microsoft Ignite presentation.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.