News
Enterprise Guidance for Moving Away from SHA-1 Encryption
Microsoft last week has released a guide for orgs looking to get away from the risky Web-based Shell Hashing Algorithim-1 (SHA-1) encryption.
A new user's guide on SHA-1 deprecation (in PDF format) was announced this week in this blog post. Also, Microsoft this month provided information for organizations using Windows 7 or Windows 8.1 on how they can test the effects of SHA-1 deprecation in advance, as detailed in this Microsoft Edge team blog post. There's also a main Microsoft reference publication on the SHA-1 transition, which can be found in this Microsoft wiki post.
Google, Mozilla and Apple are all involved in removing support for SHA-1 in their browsers, as well as Microsoft. SHA-1 hashes have long been used with digital certificates to secure Web sessions, but many software vendors have been working to phase out SHA-1 use in their products in favor of using the SHA-2 hash family instead.
Security researchers have reported that SHA-1 is potentially compromised and is subject to man-in-the-middle types of attacks. An attacker would have to perform hash collision analyses to generate the same hash output for use in fraudulent purposes. However, it's considered mathematically possible to accomplish this feat with SHA-1.
The National Institute of Standards and Technology (NIST) has advocated using the SHA-2 family of hash functions instead (PDF). NIST, a standards group that's part of the U.S. Department of Commerce, actually warned in an earlier document (PDF) that SHA-1 use should be considered "unacceptable" after 2013:
Some applications, such as signing a public key certificate, are very high risk and the use of SHA-1 in those applications should be avoided as much as possible. In NIST’s view, after 2013, the risk is unacceptable in all applications, and the use of SHA-1 when generating a digital signature is not allowed after that date.
Microsoft has announced details about its general SHA-1 deprecation plan, including an announcement back in May that the lock icon in its browser would not appear when SHA-1 technology was being used, starting in the summer of 2016. That phase is already in effect.
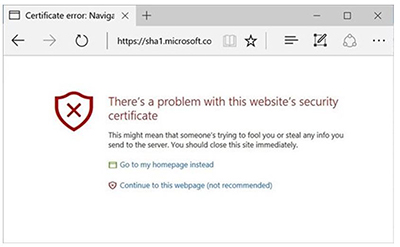
The next phase is slated for Feb. 14, 2017, when Microsoft's software products get updated. At that point, users of Microsoft Edge or the Internet Explorer 11 browser will see a warning about a Web site's security if SHA-1 technology was used. The use of the SHA-1 certificate won't be blocked. Instead, users will see options in their browser, including a not-recommended option to proceed to the Web site. The warning will look like this screenshot:
 [Click on image for larger view.]
Microsoft browser message expected to appear in February when accessing sites using deprecated SHA-1 technology.
[Click on image for larger view.]
Microsoft browser message expected to appear in February when accessing sites using deprecated SHA-1 technology.
This change in behavior will only be in effect for "SHA-1 certificates that chain to a Microsoft Trusteed Root CA [Certificate Authority]," according to Microsoft's user guide. Certificates that were manually installed by an organization or self-signed won't be affected by this change of behavior. The exception also applies to certificates that were "cross-signed with a Microsoft Trusted Root."
Also, the February 2017 software updates won't affect older Internet Explorer browser versions or third-party Windows applications "that use the Windows cryptographic API set," the Microsoft Edge team explained.
A third phase will kick in at a certain point in which SHA-1 use will be distrusted "throughout Windows in all contexts" for Internet Explorer 10 and older versions, as well for other applications. The date when this third phase will happen is yet to be announced by Microsoft.
Organizations that have installed the November Windows updates for Windows 7 and Windows 8.1, including the preview of the monthly rollup issued in November, will have the capability to test these coming changes in advance. The steps to carry out those tests are illustrated in Microsoft's Edge team post.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.