PowerShell Pipeline
Automate WSUS Using the PowerShell UpdateServices Module
Managing the WSUS has evolved over the course of the years from a Web page to using a MMC which still connects to the WSUS on either port 80 or 443 (as well as 8350 and 8351 as alternate ports). Automating and managing the clients and updates through the MMC, while still a viable option, can be time consuming and doesn't allow for easy reporting of the state of the updates or clients.
Using PowerShell, we can automate update approvals, or decline updates which are not useful for our network like the Itanium updates. We can also generate reports which may not be as easy to do using the built-in reports on the WSUS console.
To begin working with WSUS, we need to import the UpdateServices module. Note that this module is available on Windows 2012 and above as well as Windows 8 and above. Once we have the module installed on the system, we can load the module via Import-Module.
Import-Module -Name UpdateServices
We can take a quick look at the commands by running the following command:
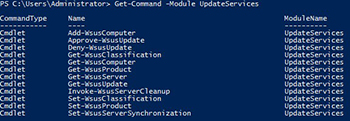
Get-Command -Module UpdateServices
 [Click on image for larger view.] Figure 1.
[Click on image for larger view.] Figure 1.
We can see that there are 12 cmdlets which cover actions such as setting the schedule for synchronization to declining updates to approving updates.
WSUS Server Information
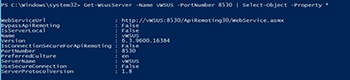
First off, we can review some information about our WSUS server by using the Get-WSUSServer cmdlet. If you are running the command locally, you do not need to specify anything, but if you need to run it against a remote WSUS server, then specifying the –Name and –Port parameter will be required.
Get-WSUSServer -Name vWSUS -Port 8530
 [Click on image for larger view.] Figure 2.
[Click on image for larger view.] Figure 2.
Gathering WSUS Computer Information
If we needed to quickly get a look at all of the clients that reside on the WSUS server, we can make use of Get-WSUSComputer to provide a report on demand.
 [Click on image for larger view.] Figure 3.
[Click on image for larger view.] Figure 3.
It's not just a lis of all clients that we can get information on. We can find out which clients had updates which failed to update as well using the –ComputerUpdateStatus parameter and specify a value of 'Failed.'
Get-WsusComputer -ComputerUpdateStatus Failed
 [Click on image for larger view.] Figure 4.
[Click on image for larger view.] Figure 4.
Viewing Updates
Viewing the updates on a WSUS server is as simple as running the Get-WSUSUpdate cmdlet and specifying certain parameters to narrow down the scope of what kind of updates you wish to display.
 [Click on image for larger view.] Figure 5.
[Click on image for larger view.] Figure 5.
Calling Get-WSUSUpdate without specifying anything will bring back all of the updates that are on the WSUS server. Note that it may take some time to bring everything back, so use this approach with caution.
A more common approach would be to find out all of the updates which have yet to be approved for installation and are needed by some of your systems. For that, we will specify an –Approval of Unapproved and the –Status of Needed.
Get-WsusUpdate -Approval Unapproved -Status Needed
 [Click on image for larger view.] Figure 6.
[Click on image for larger view.] Figure 6.
This is a quick way of reporting on updates which should be reviewed and then approved for installation so all of your systems can remain up to date with their patches.
Approving Updates from WSUS
We can then make use of Approve-WSUSUpdate by passing each of the updates found using Get-WSUSUpdate into this cmdlet to ensure that these updates will be available for installation on the systems that require them.
Get-WsusUpdate -Approval Unapproved -Status Needed |
Approve-WsusUpdate -Action Install -TargetGroupName 'All Computers' -WhatIf
In this case, I used –WhatIf just to simulate what would happen if I approved all of these updates. When you are ready to roll with the approvals, simply remove –WhatIf and all of the updates will be approved and downloaded to each system that falls under the 'All Computers' target group, which is actually all of the clients in WSUS.
Declining Updates
It's not just approving updates in WSUS that we can take advantage of the output of Get-WSUSUpdate, declining updates is useful to ensure that we managing our WSUS server efficiently. For instance with the example below, we are looking to decline all updates that have yet to been approved or declined that are language packs.
Get-WsusUpdate -Approval Unapproved -Status Any | Where {
$_.update.title -match "Language"
} | Deny-WsusUpdate –Verbose
Performing WSUS Cleanup
The last cmdlet that I will cover here is the Invoke-WSUSServerCleanup cmdlet which gives you multiple options of cleanup types that you can choose from. You can one or all of the available options to perform a cleanup on your server. In my case, I am going to run all of the available options to keep my WSUS server running lean and mean.
Invoke-WsusServerCleanup -CleanupObsoleteComputers -CleanupObsoleteUpdates `
-CleanupUnneededContentFiles -CompressUpdates -DeclineExpiredUpdates -DeclineSupersededUpdates
 [Click on image for larger view.] Figure 7.
[Click on image for larger view.] Figure 7.
It took a bit of time, but the results speak for themselves. I was able to cleanup quite a bit of space and now know that my server is keeping maintained. This is something that might be useful to run as a scheduled task to ensure that you have a monthly cleanup task for WSUS.
With this knowledge of the UpdateServices module to do more with WSUS, you can begin automating some of your tasks as well as approving and declining updates easily via PowerShell instead of working through the console.
About the Author
Boe Prox is a Microsoft MVP in Windows PowerShell and a Senior Windows System Administrator. He has worked in the IT field since 2003, and he supports a variety of different platforms. He is a contributing author in PowerShell Deep Dives with chapters about WSUS and TCP communication. He is a moderator on the Hey, Scripting Guy! forum, and he has been a judge for the Scripting Games. He has presented talks on the topics of WSUS and PowerShell as well as runspaces to PowerShell user groups. He is an Honorary Scripting Guy, and he has submitted a number of posts as a to Microsoft's Hey, Scripting Guy! He also has a number of open source projects available on Codeplex and GitHub. His personal blog is at http://learn-powershell.net.